Protecting your personal information online starts with understanding the language of the Internet. From the secret dark web to the nuances of email etiquette, we analyze five key technical terms that directly affect online privacy.
Learning these concepts will help you navigate the Internet more safely.
Look forward to it more In this series We’ll answer the number one questions you can get from readers like you, diving deep into privacy-related technical terms and other important concepts!
People working on laptops (Kurt “Cyberguy” Knutsson)
Dark web
The hidden internet beneath the surface
Browse daily under the familiar internet Dark Web is a hidden layer of the Internet that is not indexed by search engines such as Google and requires access by professional software such as the Tor browser.
Developed by the US Navy in the 1990s for safe and anonymous communication, The Dark Web has since emerged as a paradise for privacy advocates, journalists, whistleblowers, and a hot spot for cybercriminals engaged in illegal activities. It has evolved into a hot spot for. .
Some people use the dark web for legitimate purposes, such as bypassing censorship and protecting free speech, but that is Stolen personal data, Financial fraud and illegal products, Make it a high risk zone Personal information theft.
If you want to protect your personal information from purchases, sales, or leaks on the Dark Web, consider using an ID monitoring service that scans the underground forum and databases to scan publicly available data.
If you want to make sure your data is away from malicious hands and from the dark web, Consider an ID monitoring service that allows you to scrutinize and delete the internet for your data.

Hacker illustration on the dark web (Kurt “Cyberguy” Knutsson)
Best antivirus for Mac, PC, iPhone and Androids – CyberGaipic
Encryption
If you secure a digital world, one at a time
Have you ever wondered how secure your online banking information is? This is the process of scrambling data into secret code thanks to encryption, so only certified people (or devices) can be read.
How encryption works:
- Turn data into unreadable text – If intercepted, it looks like gibberish.
- Only the appropriate system can unlock – Your bank, email provider, or messaging app will automatically decrypt, so you will see regular text.
Where to use encryption every day:
- Secure websites – Find it https (“S” means it is encrypted).
- Messaging Apps – Using WhatsApp and Imessage End-to-end encryption.
- Online Banking and Shopping – Protect your financial transactions.
The encryption is preserved Practicing eyes And your personal information is safe, as everything you do online should not be open book. Check out other tips to protect your documents and keep them private.
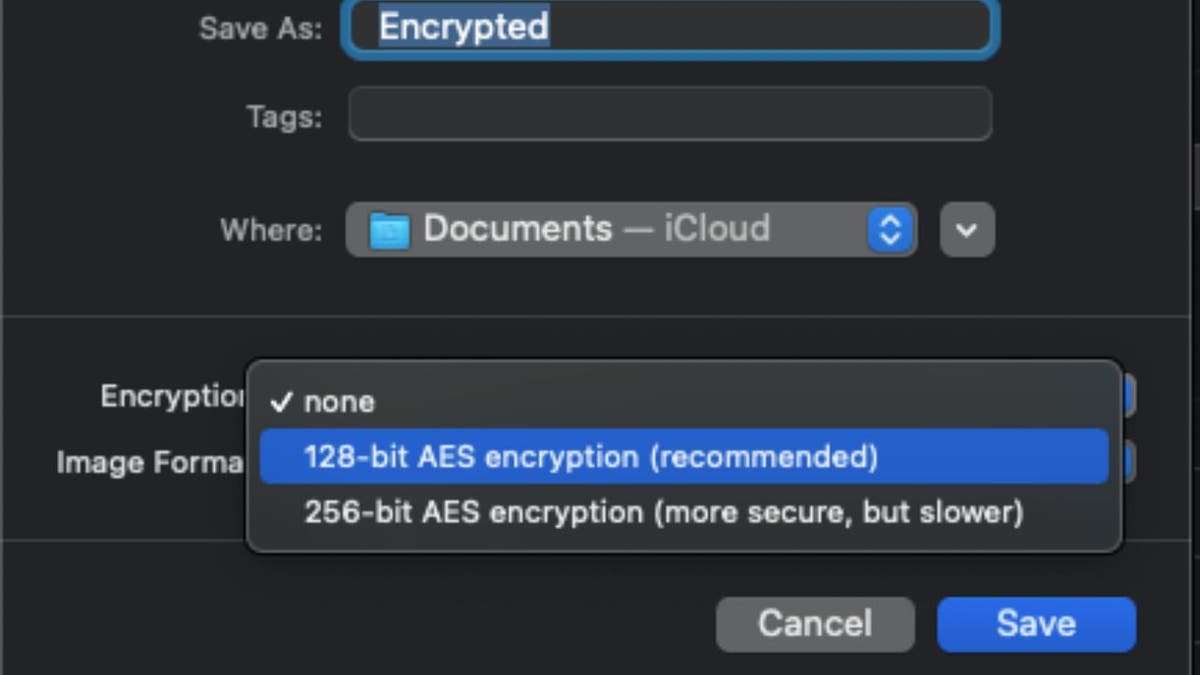
Store documents with encryption (Kurt “Cyberguy” Knutsson)
Capture
Prove that you are human online
Did you need to click on the signal photo or enter wavy text before logging on the website? It’s a capture, A simple test designed to separate humans from bots.
On websites, using CaptChas, automated programs (such as Spambots) block access to your account, submit fake forms, or post junk. The name refers to “aparting computers and humans in a fully automated public Turing test.”
So, what is the Turing Test? Named after Alan Turing, a computer scientist and WW2 codebreaker, it’s difficult to see if machines work like humans and people can’t convey the difference. Captures flip the idea and make sure you’re a human, not a bot!
Some captures ask you to solve the puzzle, but the newer versions should check if the mouse movements look human. The next time you prove that you are “not a robot”, you are actually helping to protect the internet.
However, not all captures are created equally. Follow my guide to learn how to find fake capture signs designed to download malware.

Websites using Captcha (Kurt “Cyberguy” Knutsson)
Best Techniques for Personal Protection in 2025
spam
From Monty Python to Malware: The Evolution of Spam
term “spam” Unwanted emails come from Monty Python sketches, where the word “spam” (see canned) is repeatedly mentioned and overwhelmed the conversation. This led to the term used to describe the overwhelming nature of Unnecessary email: Spam.
Originally, Spam was an annoying flood inbox with promotional emails, chain letters and unrelated ads. But over time, spam has evolved into a major cybersecurity threat. Fishing Email, Attachments containing malware And then, fraudulent schemes are hiding in spam messages, clicking malicious links to unsuspecting users to reveal sensitive information or infecting devices with ransomware or spyware .
What is Artificial Intelligence (AI)?

Woman encountering spam on laptop (Kurt “Cyberguy” Knutsson)
CC/BCC
Who sees what? Mastering email copy
Believe it or not, you may already know what the nicknames for these technical terms came from. If you’ve ever sent an email, you’ve probably seen CC and BCC. But what are they for?
CC stands for “carbon copy,” a throwback to the era of typewriters when carbon paper made replica copies. Email means sending a copy of your message to someone so they can provide you with information. Everyone can see who is CC’d and is perfect for keeping people in a loop without needing a response.
Click here to get your Fox business on the go
BCC stands for “blind carbon copy.” It’s like CC, but private. Recipients in the BCC field will receive an email, but their name and address are not visible to others. This is useful for group emails that want to protect your privacy and avoid a response storm.
These tools help you manage your communication and keep everyone on the same page. Want to switch your email provider to a safer, more private platform? Check out my picks – I’ll take you with pros and cons.
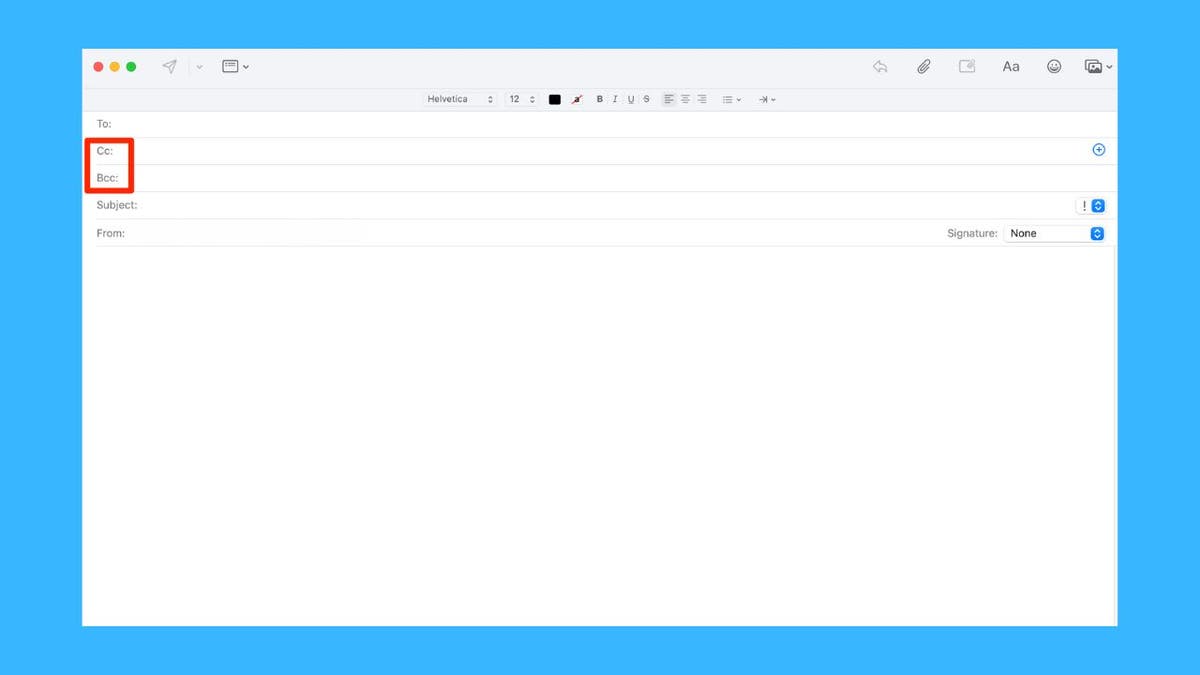
CC/BCC is outlined in red (Kurt “Cyberguy” Knutsson)
Important takeouts for your cart
It is essential to understand these five privacy-related technical terms. Dark Web emphasizes the need to protect personal data. Encryption is a digital shield that protects your information during online activities. Captchas helps to protect your website from automated attacks. This indirectly preserves security. Recognizing spam protects you Fishing and Malware. Also, using CC and BCC properly in emails respects privacy. Knowing these concepts gives you the equipment to enhance your online privacy and security.
Click here to get the Fox News app
Are you confused by technical terms or want to explain something? We want to hear from you! Share your question on cyberguy.com/contact So we can help.
For more information about my tech tips and security alerts, sign up for our free Cyberguy Report Newsletter cyberguy.com/newsletter
Ask us a question in our cart or let us know what you want us to cover
Follow your cart on his social channels
Answers to the most asked Cyber Guy questions:
New from Cart:
Copyright 2025 cyberguy.com. Unauthorized reproduction is prohibited.


