If there’s one thing that’s been revealed over the past year, then Apple devices aren’t as secure as the company wants you to believe.
We’ve been four months since 2025 and we already have over 10 instances where attackers are targeting Apple users in particular, these are just incidents we know.
I’ll admit that the device is not innocent, but it appears there’s a growing trend in which bad actors prefer to target Apple users over other platforms. In fact, security researchers have recently identified a new phishing campaign where previously focused on Windows hackers have set their sights on Apple IDs.
People working on Apple laptops (Kurt “Cyberguy” Knutsson)
What you need to know
Security researcher of layerx lab We discovered a new phishing campaign targeting MAC users and marked a shift from the previous Windows focus. The attacker initially invited Windows users with fake Microsoft security alerts designed to steal login credentials. However, after Microsoft, Chrome, and Firefox implemented new security features to block these attacks, hackers instead began redirecting efforts to Mac users.
The new attack closely reflects its predecessor, but there are significant changes. The phishing page has been redesigned to resemble Apple’s security warnings, making it look legal to MacOS users. The attack code is tailored to specially detect MacO and Safari users, allowing only Apple users to view malicious pages.
Furthermore, despite shifting focus, attackers continue to host these phishing pages on Microsoft’s Windows[.]Net domain. Because this is a reliable Microsoft platform, you can avoid phishing pages with security tools that assess risk based on domain reputation.
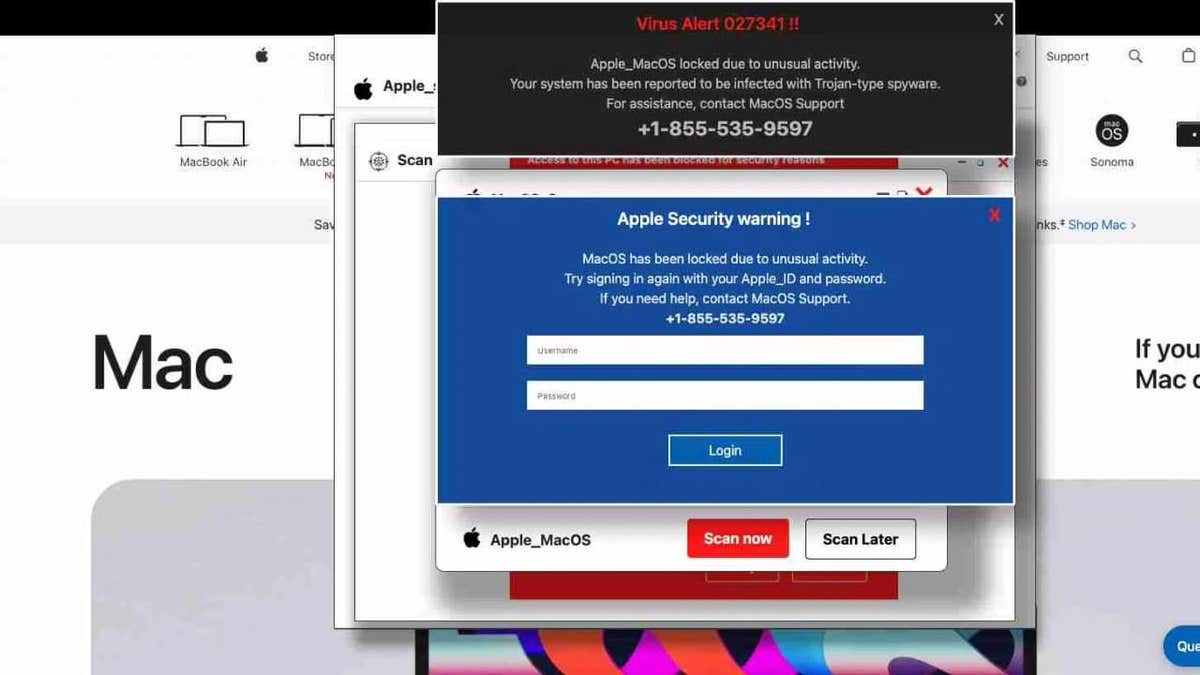
Breaked websites displaying fake security warnings (layerx)
The FBI warns about a dangerous new “smissing” scam targeting your phone
How victims are seduced
Phishing campaigns utilize a common yet highly effective method known as typecutting and malicious redirection. Victims often appear on these phishing pages after making simple mistakes, such as making a mistake in a URL while trying to access a legitimate website.
Instead of reaching the intended site, you land on the compromised domain parking page. From there, they are redirected through multiple websites before they finally arrive at the phishing page. This presents a fake Apple security warning. If they believe their Apple IDs are at risk, the victims are tricked into entering their credentials, and unwittingly hand them over to the attacker.
One notable case involved people using Safari who worked in a business protected by a secure web gateway. Despite the organization’s security measures, phishing attempts have managed to bypass the protection of the gateway.
What is Artificial Intelligence (AI)?
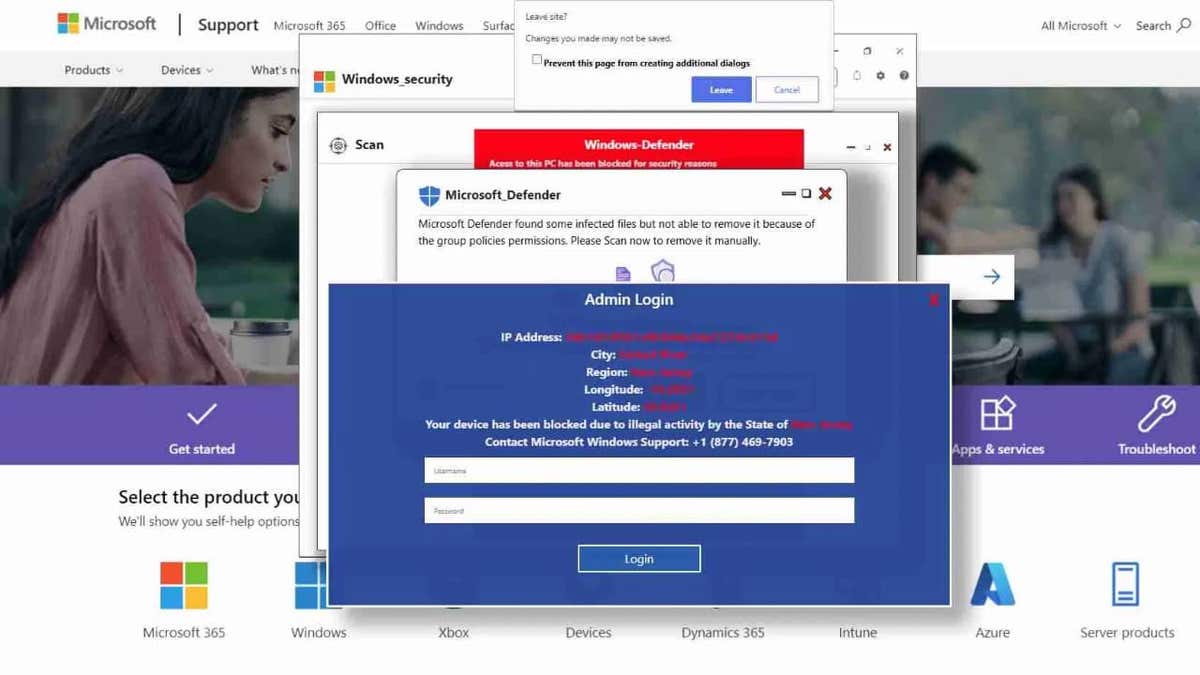
Breaked websites displaying fake security warnings (layerx)
Apple’s iOS vulnerability exposes iPhone to stealth hacker attacks
Seven Ways to Stay Safe from Attackers Targeting Apple Users
Phishing campaigns are increasingly targeting MacOS users, but you are not vulnerable. Here are four important steps to protect yourself.
1. Use powerful antivirus software. A trusted antivirus program is your first line of defense against phishing attempts and malicious websites. Apple’s built-in security features provide some protection, but they are not innocent, especially against sophisticated phishing attacks that mimic legitimate Apple warnings. A robust antivirus solution can detect and block malicious sites before even reaching them, preventing them from accidentally entering their credentials on malformed pages. Additionally, Advanced Security software can identify and warn suspicious redirects before becoming victim to a type skate trap. Get the best 2025 Antivirus Protection Winners picks for Windows, Mac, Android and iOS devices.
2. Keep your software up to date: usually Updates to MacOS and applications It’s not just new features. They are important patches that fix security vulnerabilities. The attacker quickly exploits all weaknesses, ensuring that the operating system and all installed software minimize the risk of violations. Automatic updates are enabled whenever possible, so you’re always protected by the latest security enhancements.
3. Monitor Apple ID activity regularly. Even with strong security in place, it is important to keep an eye on your Apple ID account for signs of unauthorized access. With Apple, users can view account activity, including devices recorded in their accounts and recent changes. Check your Apple ID settings regularly to ensure that only trusted devices are connected and that no suspicious activity is occurring. If you notice anything unusual, such as trying to log in from an unfamiliar location, immediately change your password and remove the incorrect device. This aggressive approach helps you acquire potential violations early and minimize damage.
Click here to get your Fox business on the go
4. Enabling 2-factor authentication (2FA): Strong and unique passwords for all accounts are essential, but they are even more effective Two-factor authentication. Even if an attacker could steal your qualifications through a phishing attack, 2FA It adds additional barriers that make unauthorized access much more difficult. Consider using Password Manager Generate and store complex passwords. Get my details Find the best expert reviewed password managers of 2025 here.
5. For added security, use a recovery key. Apple offers an optional feature called Recovery Key, a 28-character code that provides an additional layer of security for your Apple ID. When you enable the recovery key, Apple disables the standard account recovery process. This means that you will need this key along with access to a trusted device or phone number to reset your password or regain access to your account. This makes it extremely difficult for an attacker to control the account.
To set the recovery key, go to Settings> [Your Name] >Sign in & Security > Recovery Key On your iPhone, iPad, or Mac. Follow the prompts to generate and confirm the recovery key. Write it down and store it in a safe place, such as a reliable family. Please note that if you lose both your recovery key and access to a trusted device, you can permanently lock out your account. However, if used responsibly, this feature gives you greater control over your account security.
6. Enabling biometric authentication: Apple devices are highly offered Biometric options such as Face ID and Touch IDproviding an extra layer of security. These features allow attackers to access devices and sensitive accounts, even if they can steal credentials. It allows biometric authentication whenever possible, especially for apps and services that store personal and financial information. Biometric data is unique to you, which adds a level of protection that cannot be provided with a password alone.
7. Practice safe browsing: Many attacks rely on simple user mistakes, such as incorrect typing in a URL or clicking suspicious links. Always make sure you are accessing legitimate websites before entering any personal information. Even if you mimic Apple’s design, you’re skeptical of unexpected security alerts. Learning to identify subtle signs of phishing like unusual URL structures and general greetings will help you avoid falling into these scams.
How to protect your iPhone and iPad from malware
Important takeouts in your cart
For a long time, Apple has sold the idea that its ecosystem is inherently safer than its alternatives, but its claims are beginning to fade. The reality is that attackers are no longer ignoring Mac users, they are actively targeting targets, and Apple’s response is not aggressive. While Microsoft, Google and others are taking new security measures to combat evolving threats, Apple remains slow to adapt, relying on outdated assumptions about platform safety.
Click here to get the Fox News app
Do you think Apple should be more transparent about security vulnerabilities that affect users? Write us and let us know cyberguy.com/contact.
For more information about my tech tips and security alerts, sign up for our free Cyberguy Report Newsletter cyberguy.com/newsletter.
Please ask your cart or tell us what stories you would like us to cover.
Follow your cart on his social channels:
Answers to the most accused Cyber Guy questions:
New from Cart:
Copyright 2025 cyberguy.com. Unauthorized reproduction is prohibited.


