Clickfix is a social engineering trick that hackers are increasingly using to spread malware in early 2024.
It tricks you into running malicious commands on your own computer, and attacks have become more common than ever. Hackers have them install password-stolen malware by pressing a series of keyboard shortcuts under the pretense of proving they’re not bots.
A bot is an automated computer program that performs repetitive tasks online, and often mimics human behavior. By tricking you into proving they’re not bots, hackers will exploit the lack of understanding about these automated systems to unconsciously install malware.
People who work on laptops (Kurt “Cyberguy” Knutsson)
What you need to know
As reported by Krebsonsecuritythe latest ClickFix campaigns will start installing password-steel malware under the guise of a routine “Ensure you are human” test. Initially, it was seen in targeted attacks, but now it has become mainstream and has impacted industries such as hospitality and healthcare.
Scams start when you visit hacked or malicious websites and see fake Captcha-style prompts.[私はロボットではない]Clicking the button triggers a series of instructions asking you to press a specific keyboard shortcut. First, you are told to press Windows + R and the Windows Run dialog opens. You will then be told to press Ctrl + V to paste the malicious script copied from the virtual clipboard of your website. Press Enter and it will run a script that downloads and runs the malware.
What is Artificial Intelligence (AI)?
Cybercriminal uses phishing emails and malicious websites to spread Clickfix. The hospitality industry is highly targeted, with attackers impersonating Booking.com and sending fake emails referring to guest reviews and promotions. Click on these email links to see a Clickfix trap. Healthcare workers are also targeted, with malicious code embedded in the widely used physical therapy site HEP2GO.
When Clickfix comes onto your PC, it installs a variety of malware, including password steelers such as Xworm, Lumma Stealer, and Danabot. Some versions provide remote access trojans such as Venomrat and Asyncrat, allowing attackers to have full control over the system. Others deploy NetSupport rats, a remote access tool commonly misused for cyber espionage.
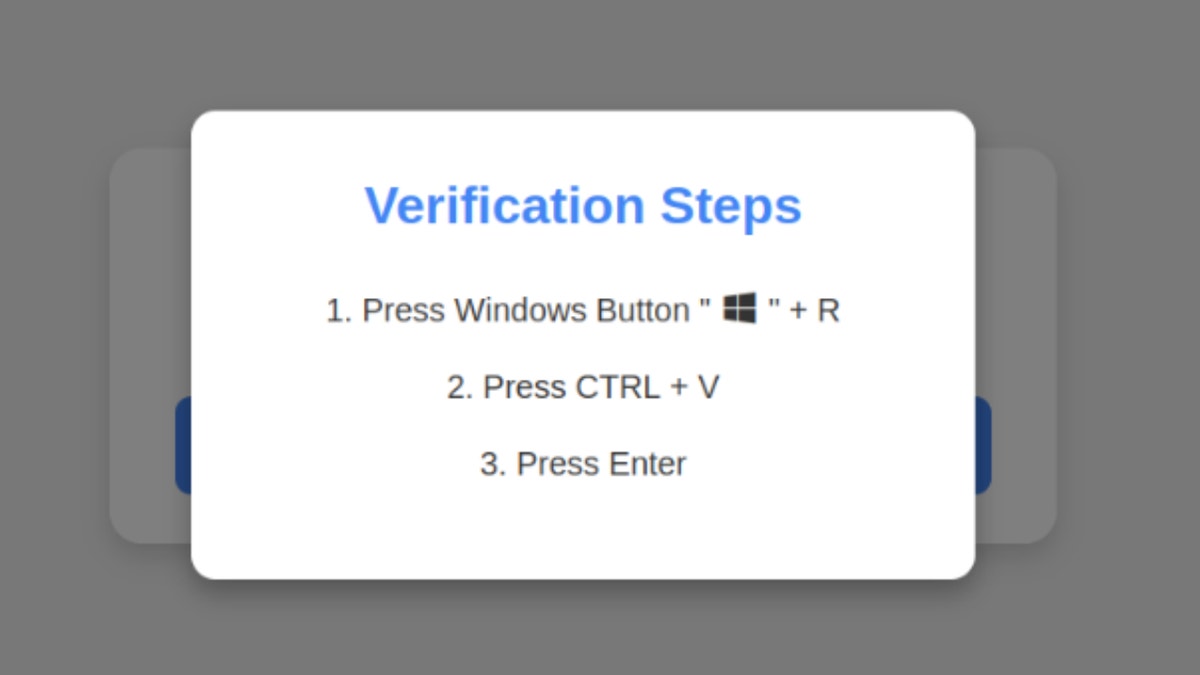
Running a keypress for this series will prompt Windows to download password stealing malware. (Krebsonsecurity)
Hidden Costs of Free Apps: Your Personal Information
Previous clickfix attacks
Security researchers believe Clickfix will be targeting people from March 2024. We reported on malware in June 2024. Posing as fake Google Chrome, Word, and OneDrive errors Deceive users to download harmful code. Just like in the current campaign, the attacker prompted the victim to click on the button that copied “Fix” to the clipboard and then paste it and run it in a dialogue or PowerShell prompt.
By November 2024, attackers We’ve expanded our goal to Google Meet users. The scam started with an email containing a link to a Google meeting session, but was often disguised as being seen from the victim’s organization. This link can lead to invitations for meetings, webinars, or online collaborations. Clicking on the link pointed the victim towards a fake Google Meet page. This gave a warning claiming there was a problem with the PC, such as a microphone, camera, or headset issue.
The attack was also seen on fake Chrome error pages and Facebook login prompts, spreading the malware even further to different platforms, increasing its reach.
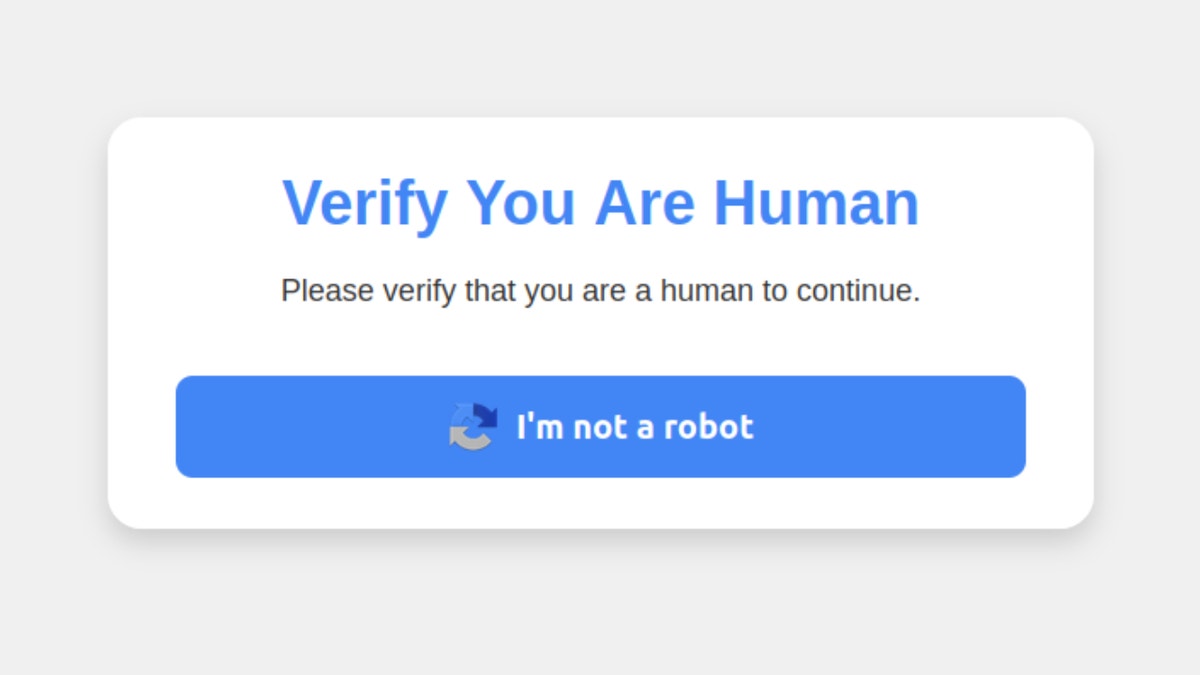
This malware attack pretends to be a capture aimed at separating humans from the bot. (Krebsonsecurity)
Outmart hackers trying to steal your identity
Six ways to stay safe from ClickFix malware
Consider implementing these six key security measures to protect yourself from the evolving threats of ClickFix malware that continue to target users through sophisticated social engineering tactics.
1. Be skeptical of Captcha’s prompt. A legitimate Captcha test doesn’t require you to press Windows + R, copy commands, or paste them into PowerShell. If the website tells you to do this, it’s probably a scam. Close the page immediately and avoid interacting with it.
2. Do not use powerful antivirus software by clicking on the link from an unverified email. Many clickfix attacks start with phishing emails pretending to be trustworthy services such as Booking.com or Google Meet. Be sure to check the sender before clicking on the link. If your email appears urgent or unexpected, instead of clicking on the link in the email, go directly to the company’s official website.
Click here to get your Fox business on the go
The best way to protect yourself from malicious links to install malware is to install powerful antivirus software on all your devices, as it may access your personal information. This protection can also warn you that it will phish email and ransomware scams and keep your personal information and digital assets safe. Get the best 2025 Antivirus Protection Winners picks for Windows, Mac, Android and iOS devices.
3. Enable 2-factor authentication. Enable Two-factor authentication Whenever possible. This adds an additional layer of security by requiring validation of the second form, including the password, as well as the code sent to the phone.
4. Update your device: Regularly Update your operating system, browser and security software Make sure you have the latest patches for known vulnerabilities. As cybercriminals take advantage of outdated systems, enabling automatic updates is an easy and effective way to stay protected.
5. Monitor your account for suspicious activity and change your password. If you interact with suspicious websites, phishing emails, or fake login pages, check your online account for unusual activity. Look for unexpected login attempts, unauthorized password resets, or unrecognized financial transactions. If you think something is missing, change your password immediately and report your activity to the relevant service provider. Also, consider using a password manager to generate and store complex passwords. Get my details Find the best expert reviewed password managers of 2025 here.
6. Investing in Personal Data Deletion Services: Please consider using services that monitor your personal information and warn you of potential violations or misuse of your data. These services can provide early warning signs of identity theft and other malicious activity resulting from Clickfix or similar attacks. Although there is no service that promises to delete all data from the internet, deleting a deletion service is great if you want to constantly monitor and automate the process of continuously deleting information from hundreds of sites over a long period of time. Check out our top picks for data deletion services.
Massive security flaws put the most popular browsers at risk with MAC
Important points of cart
ClickFix reminds us that malware doesn’t always depend on complex exploits. In many cases, you need to follow the wrong instructions. Attackers are improving their methods and are more persuading than ever before scams such as fake captures, phishing emails, and deceptive pop-ups. The best way to go ahead is to question what appears to be a little farther away. If the website runs a command or asks you to paste something into PowerShell, it’s a red flag. If your email pressures you to click on a link, check first.
Click here to get the Fox News app
Do you think tech companies are doing enough to stop malware like Clickfix? Write us and let us know cyberguy.com/contact.
For more information about my tech tips and security alerts, sign up for our free Cyberguy Report Newsletter cyberguy.com/newsletter.
Please ask your cart or tell us what stories you would like us to cover.
Follow your cart on his social channels:
Answers to the most accused Cyber Guy questions:
New from Cart:
Copyright 2025 cyberguy.com. Unauthorized reproduction is prohibited.


